Ashley Madison List PDF: Unveiling The Secrets And Understanding The Controversy
The Ashley Madison list PDF has been a subject of immense interest and controversy since its emergence in 2015. The breach of the Ashley Madison website, a platform designed for extramarital affairs, exposed millions of users' personal information. This incident sparked global discussions about privacy, cybersecurity, and the ethical implications of such platforms. Understanding the Ashley Madison list PDF is not just about data; it's about comprehending the broader impact on individuals and society.
Since its release, the Ashley Madison list PDF has become a symbol of one of the most significant data breaches in history. It highlights vulnerabilities in digital security and raises questions about the responsibility of companies handling sensitive user information. For individuals affected, the breach had profound consequences, impacting personal and professional lives.
While the Ashley Madison list PDF remains a contentious topic, exploring its origins, implications, and lessons learned is essential. This article delves into the breach's details, the data involved, and the broader implications, offering insights for individuals and businesses alike.
Understanding the Ashley Madison Breach
The Ashley Madison breach occurred in 2015 when a hacker group known as "The Impact Team" infiltrated the platform's database. The breach exposed over 32 million user accounts, including personal information such as names, email addresses, and physical addresses. The hackers released the data publicly, making it accessible in the form of an Ashley Madison list PDF.
How the Breach Happened
The hackers exploited vulnerabilities in Ashley Madison's security protocols, gaining unauthorized access to the platform's database. Despite the company's claims of secure data handling, the breach revealed significant flaws in their cybersecurity measures. The breach highlighted the importance of robust security practices and the need for companies to prioritize user data protection.
- Hackers targeted outdated security systems.
- Weak password encryption contributed to the breach.
- Lack of regular security audits made the platform vulnerable.
Data Exposed in the Ashley Madison List PDF
The Ashley Madison list PDF contained a wealth of sensitive information about users. The data included personal details such as full names, email addresses, physical addresses, and even credit card information for some users. The exposure of this data had far-reaching consequences, affecting not only individuals but also their families and professional lives.
- Sparkly Green Eyeshadow
- Boobs In Space
- 300 Pound Bench Press
- Nails Fall 2024
- Special First Birthday Gift
Types of Data Included
- Full names and contact details.
- Encrypted passwords (later cracked by hackers).
- Credit card information for paid subscribers.
- Geographical location data.
For many users, the breach led to public embarrassment, damaged relationships, and, in some cases, legal consequences. The incident underscored the risks associated with sharing personal information online, especially on platforms with questionable ethical standards.
Legal and Ethical Implications
The Ashley Madison breach raised significant legal and ethical questions. The company faced numerous lawsuits from affected users, citing negligence in protecting their data. Additionally, the platform's business model, which encouraged extramarital affairs, drew criticism for promoting unethical behavior.
Key Legal Cases
Several class-action lawsuits were filed against Ashley Madison, with plaintiffs accusing the company of failing to safeguard user data. Settlements were reached in some cases, with the company agreeing to compensate affected users. These legal actions highlighted the importance of accountability and transparency in the digital age.
- Class-action lawsuits in Canada and the United States.
- Settlements involving compensation for affected users.
- Regulatory scrutiny of the company's data protection policies.
Impact on Individuals and Society
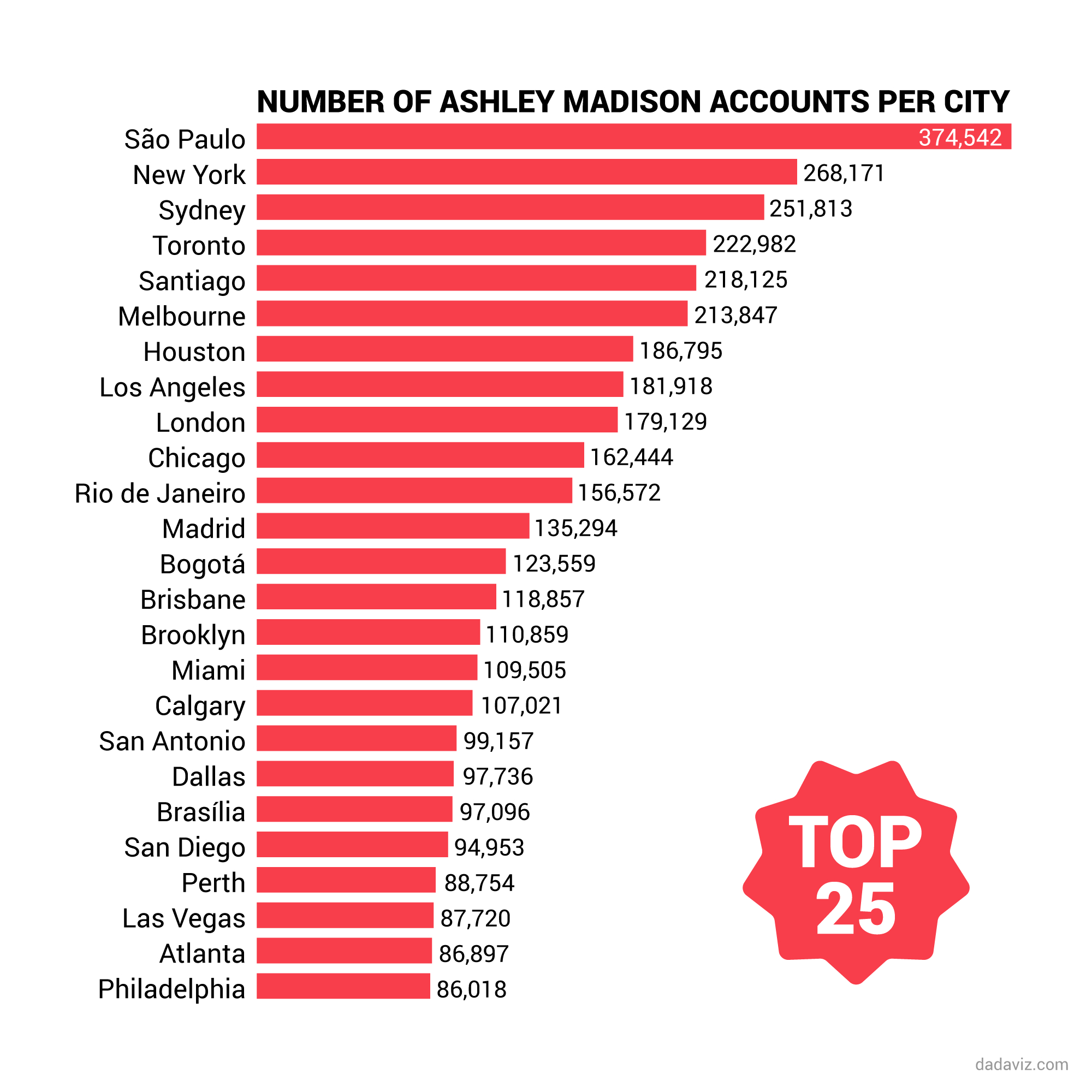
The Ashley Madison list PDF had a profound impact on individuals and society as a whole. For users affected by the breach, the consequences were often severe, leading to broken relationships, job losses, and even instances of harassment. The incident also sparked broader discussions about privacy, trust, and the ethical implications of digital platforms.
Personal Consequences
- Divorce and strained relationships due to exposed infidelity.
- Professional repercussions, including job losses and public shaming.
- Mental health challenges resulting from the breach's fallout.
Society at large began to question the role of technology in facilitating unethical behavior and the need for stricter regulations to protect user data. The breach served as a wake-up call for both individuals and organizations to prioritize cybersecurity and ethical practices.
Lessons Learned from the Ashley Madison List PDF
The Ashley Madison breach offers valuable lessons for individuals and businesses alike. It highlights the importance of robust cybersecurity measures, ethical business practices, and the need for transparency in handling user data. For businesses, the incident underscores the significance of prioritizing data protection and maintaining trust with customers.
Key Takeaways
- Implement strong cybersecurity protocols to protect user data.
- Prioritize transparency and ethical practices in business operations.
- Regularly audit security systems to identify and address vulnerabilities.
For individuals, the breach serves as a reminder to be cautious when sharing personal information online and to use strong, unique passwords to enhance personal cybersecurity.
Best Practices for Protecting Your Data
In the wake of the Ashley Madison breach, it is crucial for individuals and businesses to adopt best practices for protecting sensitive information. Implementing strong cybersecurity measures can help mitigate the risks associated with data breaches and ensure the safety of personal information.
Steps for Individuals
- Use strong, unique passwords for all online accounts.
- Enable two-factor authentication whenever possible.
- Be cautious when sharing personal information online.
Steps for Businesses
- Conduct regular security audits to identify vulnerabilities.
- Implement encryption for sensitive data storage and transmission.
- Train employees on cybersecurity best practices and protocols.
Future of Cybersecurity and Data Protection
The Ashley Madison breach marked a turning point in the evolution of cybersecurity and data protection. As technology continues to advance, the need for robust security measures becomes increasingly critical. Governments and regulatory bodies are taking steps to enforce stricter data protection laws, such as the General Data Protection Regulation (GDPR) in Europe.
Emerging Trends in Cybersecurity
- Increased adoption of artificial intelligence for threat detection.
- Focus on privacy-enhancing technologies (PETs).
- Greater emphasis on user education and awareness.
The future of cybersecurity lies in collaboration between governments, businesses, and individuals to create a safer digital environment. By learning from incidents like the Ashley Madison breach, stakeholders can work together to prevent similar occurrences in the future.
Conclusion
The Ashley Madison list PDF remains a stark reminder of the importance of cybersecurity and ethical business practices. The breach exposed millions of users' personal information, leading to significant personal and societal consequences. By understanding the breach's origins, implications, and lessons learned, individuals and businesses can take proactive steps to protect sensitive data and promote a safer digital world.
We encourage readers to share their thoughts and experiences in the comments section below. For more insights on cybersecurity and data protection, explore our other articles and resources. Together, we can create a more secure and ethical digital environment for everyone.
Table of Contents
- Understanding the Ashley Madison Breach
- Data Exposed in the Ashley Madison List PDF
- Legal and Ethical Implications
- Impact on Individuals and Society
- Lessons Learned from the Ashley Madison List PDF
- Best Practices for Protecting Your Data
- Future of Cybersecurity and Data Protection
- Conclusion
Data sources: The New York Times, BBC News, CNBC.
- How To Make It Look Like You Have Bangs
- Women S Perfume For Summer
- When Is Greys Back
- Schiaparelli Kylie Jenner
- Solawave Eye Mask Reviews
Ashley Madison List Arkansas Spreadsheet with regard to Ashley Madison

Ashley Madison List Arkansas Spreadsheet with regard to Ashley Madison
Ashley Madison List Arkansas Spreadsheet for Ashley Madison Most